Penetration Test
Workflow
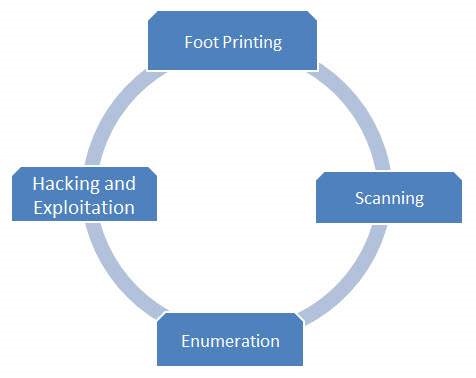
Footprinting
Footprinting is the process of gathering the blueprint of a particular system or a network and the devices that are attached to the network under consideration. It is the first step that a penetration tester uses to evaluate the security of a web application. After footprinting, a penetration tester can understand the pulse of a hacker. It is good to understand the complete system before testing its modules.
Footprinting – Steps
- Information gathering
- Determining the range of the network
- Identifying active machines
- Identifying open ports and access points
- OS fingerprinting
- Fingerprinting services
- Mapping the network
Tools Used in Footprinting
- Whois
- SmartWhois
- NsLookup
- Sam Spade
Scanning
Scanning is the second step that is performed after footprinting. It involves scanning open ports, fingerprinting the operating system, and uncovering services on ports. The ultimate goal of scanning is to find open ports through external or internal network scanning, pinging machines, determining network ranges, and port scanning individual systems.
Tools Used in Scanning
- NMap
- Ping
- Traceroute
- Superscan
- Netcat
- NeoTrace
Enumeration
Enumeration is the next step after scanning. The goal of enumeration is to get a complete picture of the target. In this phase, a penetration tester tries to identify valid user accounts or poorly-protected shared resources using active connections to systems.
Techniques Used in Enumeration
- Identifying vulnerable user accounts
- Obtaining Active Directory information
- Using snmputil for Simple Network Management Protocol enumeration
- Employing Windows DNS queries
- Establishing null sessions and connections
Exploitation
Exploitation is the last phase where a security tester actively exploits the security weaknesses present in the system under consideration. Once the attack is successful, it is possible to penetrate more systems in the domain, because the penetration testers then have the access to more potential targets that were not available before.
Techniques Used in Exploitation
The types of exploitation are segregated into three different categories −
1. Attack against WEB-SERVERS
- SQL Injection
- Cross-site Scripting
- Code Injection
- Session Hijacking
- Directory Traversal
2. Attack against NETWORKS
- Man in the Middle Attack
- Spoofing
- Firewall Traversal
- WLAN
- ARP Poisoning
3. Attack against SERVICES
- Buffer Overflows
- Format Strings
- Dos
- Authentication flaws