Reverse Tabnabbing
Description
Reverse tabnabbing is an attack where a page linked from the target page is able to rewrite that page, for example to replace it with a phishing site. As the user was originally on the correct page they are less likely to notice that it has been changed to a phishing site, especially if the site looks the same as the target. If the user authenticates to this new page then their credentials (or other sensitive data) are sent to the phishing site rather than the legitimate one.
As well as the target site being able to overwrite the target page, any http link can be spoofed to overwrite the target page if the user is on an unsecured network, for example a public wifi hotspot. The attack is possible even if the target site is only available via https as the attacker only needs to spoof the http site that is being linked to.
The attack is typically possible when the source site uses a target instruction in a html link to specify a target loading location that do not replace the current location and then let the current window/tab available and does not include any of the preventative measures detailed below.
The attack is also possible for link opened via the window.open javascript function.
Overview
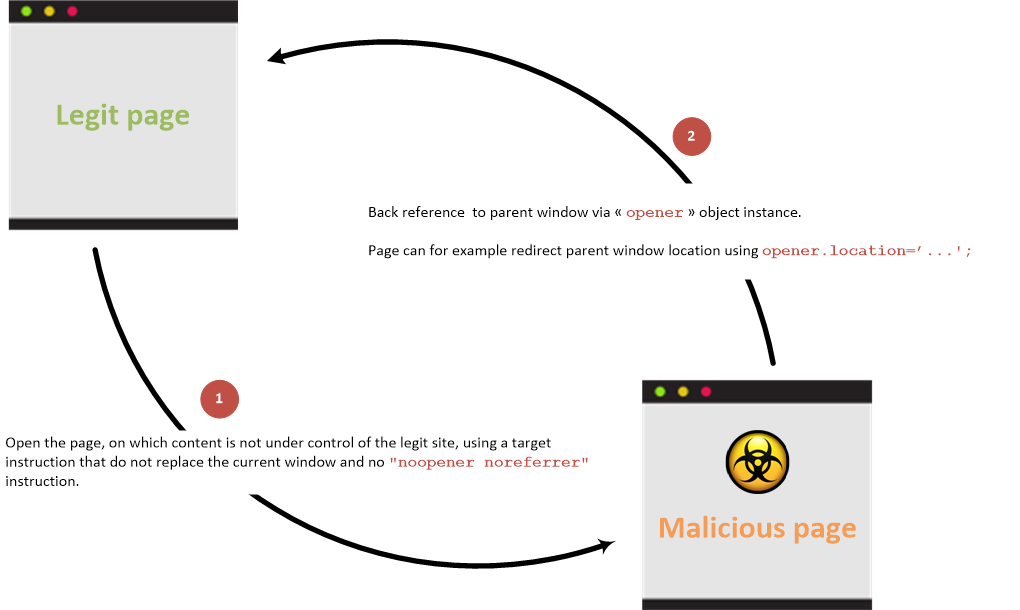
With back link
Link between parent and child pages when prevention attribute is not used:
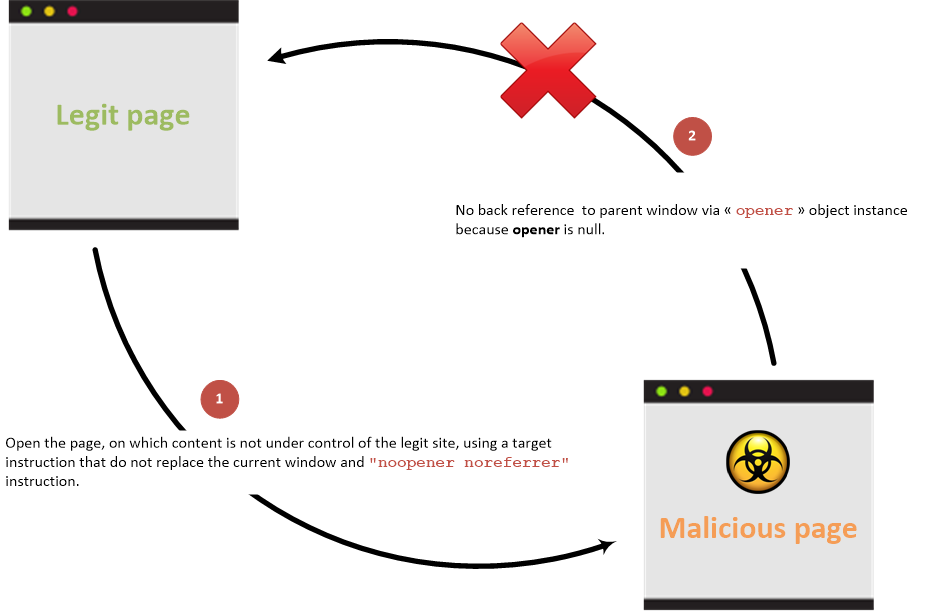
Without back link
Link between parent and child pages when prevention attribute is used:
Examples
Vulnerable page:
<html>
<body>
<li>
<a href="bad.example.com" target="_blank"
>Vulnerable target using html link to open the new page</a
>
</li>
<button onclick="window.open('https://bad.example.com')">
Vulnerable target using javascript to open the new page
</button>
</body>
</html>
Malicious Site that is linked to:
<html>
<body>
<script>
if (window.opener) {
window.opener.location = "https://phish.example.com";
}
</script>
</body>
</html>
When a user clicks on the Vulnerable Target link/button then the Malicious Site is opened in a new tab (as expected) but the target site in the original tab is replaced by the phishing site.
Prevention
This is now automatically prevented in all modern, evergreen, browsers.