Docker
Overview
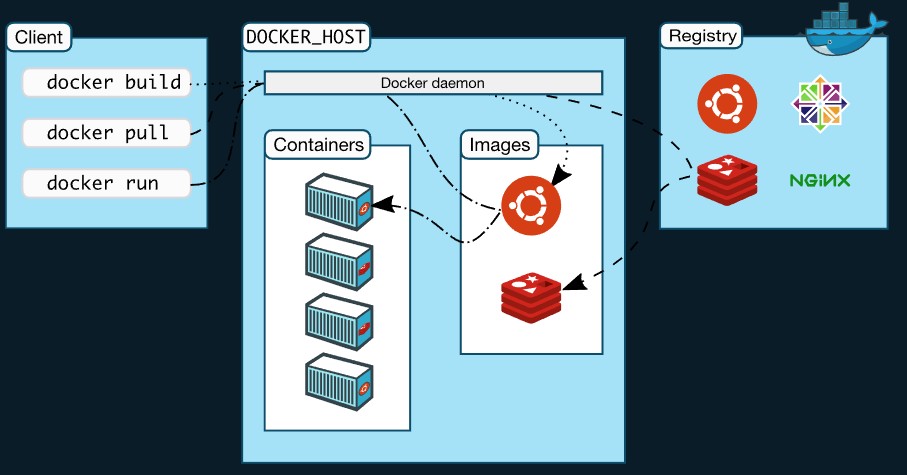
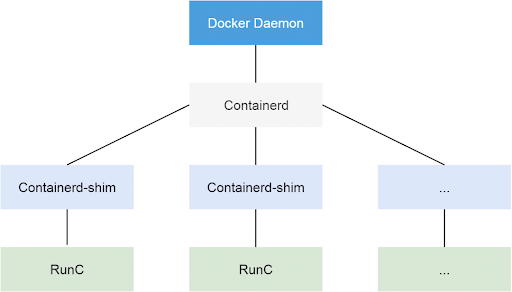
Cheat Sheet
docker build -t <image_name> .
docker images
docker run -d -p 3000:8080 --name <container_name> -e <key>=<value> <image_name>
docker ps -a
docker logs <containerID>
docker stop <containerID>
docker start <containerID>
docker exec -it <containerID> bash
docker login <registryURI>
docker cp <file> <containerID>:<path>
# Save one or more images to a tar archive
docker save <image_name> -o myapp.tar
docker save <image_name> | gzip -c > myapp.tar.gz
# Load an image from a tar archive
docker load -i myapp.tar
gunzip -c myapp.tar.gz | docker load
# Remove "none" tag images
docker image prune --filter="dangling=true"
Container Registry
Self-Hosted
- Docker Registry 2.0
- Harbor
Fully-Managed
- Google Container Registry (GCR)
Deploy a Registry Server
# Run a local registry
docker run -d -p 5000:5000 --restart=always --name registry -v /home/evan/mnt/registry:/var/lib/registry registry:2
# The first part of the tag is a hostname and port, Docker interprets this as the location of a registry, when pushing.
docker tag express-server localhost:5000/express-server
# Push the image to the local registry running at localhost:5000
docker push localhost:5000/express-server
# List images in the local registry
curl -X GET http://localhost:5000/v2/_catalog
Test an Insecure Registry
- Edit the daemon.json file, whose default location is /etc/docker/daemon.json on Linux
{
"insecure-registries": ["myregistrydomain.com:5000"]
}
Push and Deploy a Docker Image on Heroku
heroku login
heroku container:login
docker build -t registry.heroku.com/<your-app>/web .
docker push registry.heroku.com/<your-app>/web
# Deploy
heroku container:release web -a <your-app>
Minify Docker Image
docker-slim build <image_name>
Container Monitoring Tools
Docker Compose UI
Best Practices
- Use official and verified Docker Images as Base Image
- Use Specific Docker Image Versions
- Use Small-Sized Official Images
- Optimize Caching Image Layers
Order Dockerfile commands from least to most frequently changing
- Use .dockerignore file
- Make use of Multi-Stage Builds
- Use the Least Privileged User
- Scan your Images for Security Vulnerabilities
docker scout cves <image_name>